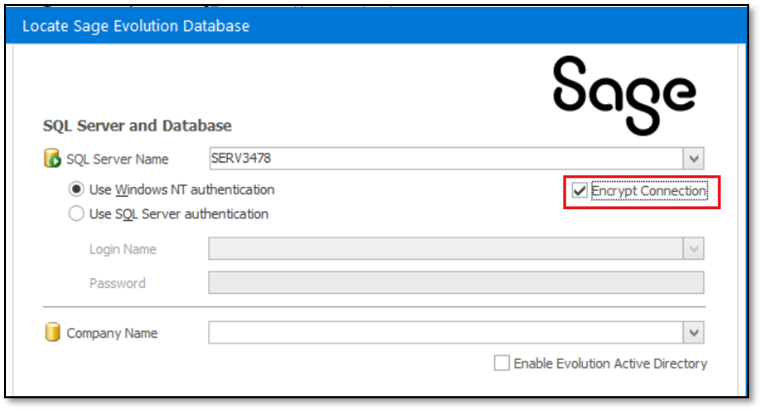
General, Company: ‘Encrypt Connection’ option on the ‘Locate Sage Evolution Database’ and ‘Edit Sage Evolution Database’ screen
Summary
Learn more about the ‘Encrypt Connection’ option on the ‘Locate Sage Evolution Database’ and ‘Edit Sage Evolution Database’ screens.
Description
This article discusses the purpose and provides further details about the Encrypt Connection option on the ‘Locate Sage Evolution Database’ and ‘Edit Sage Evolution Database’ screens.
This option is available when locating or editing a Sage 200 Evolution (Evolution) company and Common database profile (on the workstation and Evolution server).
Resolution
Consider the following advice to achieve the above outcome:
Purpose of the Encrypt Connection option
This option provides an additional layer of security between your Evolution workstations/Server and the company database residing on the MS SQL Server instance.
MS SQL Server Encryption
The Encrypt Connection option in Evolution will only be effective if you have also configured encryption on the MS SQL Server instance.
This encryption should be applied by a qualified IT technician on the SQL Server instance and network.
Open this link for details on enabling encryption on the SQL server instance.
The involvement of TLS
Usually, the TCP/IP and UDP network protocols regulate and facilitate the Sage Evolution network communication and provide standard security.
However, when your SQL Server has been configured to use encryption and the workstation has been set up accordingly (the above option enabled), the connection between the workstation and the SQL server instance will be encrypted.
In this case, the TLS (Transport Layer Security) encryption protocol is added to help protect your network.
Additional System/software requirements
Besides the above-mentioned SQL server encryption configuration, also consider the following system/software requirements:
- Self-signed certificate, or
- A purchased certificate from a trusted certification authority
There are no additional software requirements needed.
Potential limitations after activation
Enabling encryption can make the data useless without the corresponding decryption key or password.
Encryption doesn’t solve access control problems. However, it enhances security by limiting data loss even if access controls are bypassed.
Open this link for more details about a potential limitation.